43 aws best practices
Best practices for AWS accounts - AWS Account Management WebBest practices for AWS accounts. This section describes best practices that we recommend that you follow with your AWS accounts. They are arranged in the following categories: Topics. Best practices to protect your account's root user; Best practices for managing AWS access keys ; Document Conventions. Example SCPs. Root user. This … Introduction - EKS Best Practices Guides - GitHub Pages WebWelcome to the EKS Best Practices Guides. The primary goal of this project is to offer a set of best practices for day 2 operations for Amazon EKS. We elected to publish this guidance to GitHub so we could iterate quickly, provide timely and effective recommendations for variety of concerns, and easily incorporate suggestions from the broader community.
Best practices for Amazon RDS - Amazon Relational Database ... For information about best practices for working with Amazon RDS for Oracle, see Best practices for running Oracle database on Amazon Web Services. A 2020 AWS virtual workshop included a presentation on running production Oracle databases on Amazon RDS.

Aws best practices
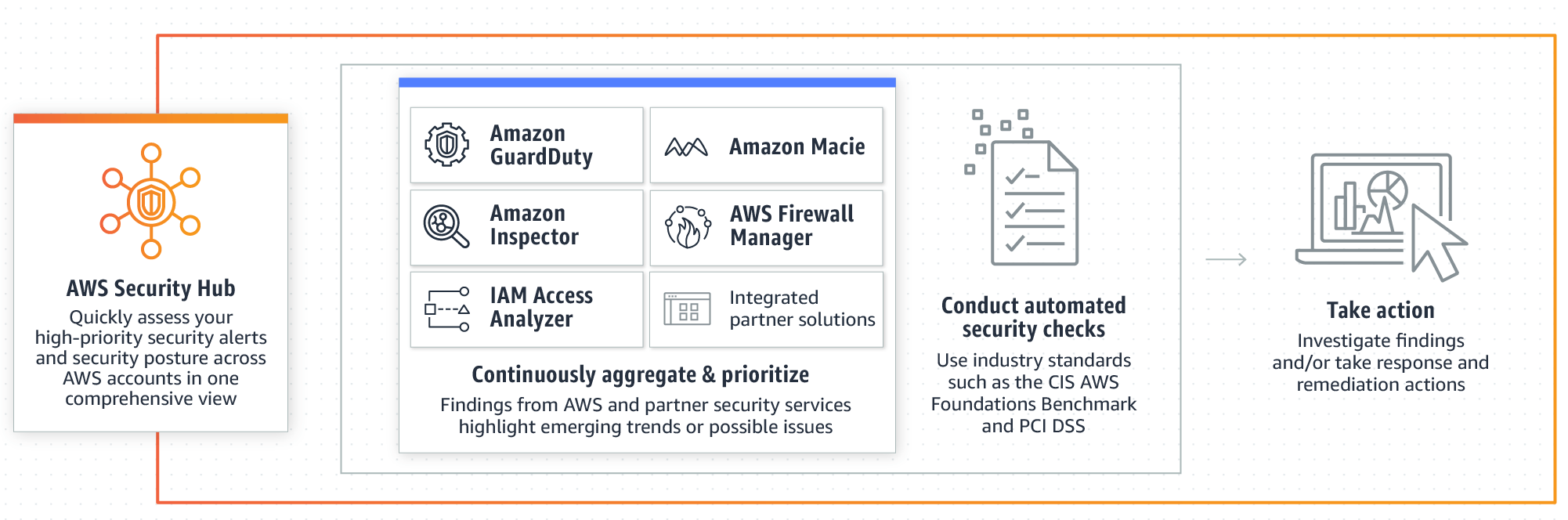
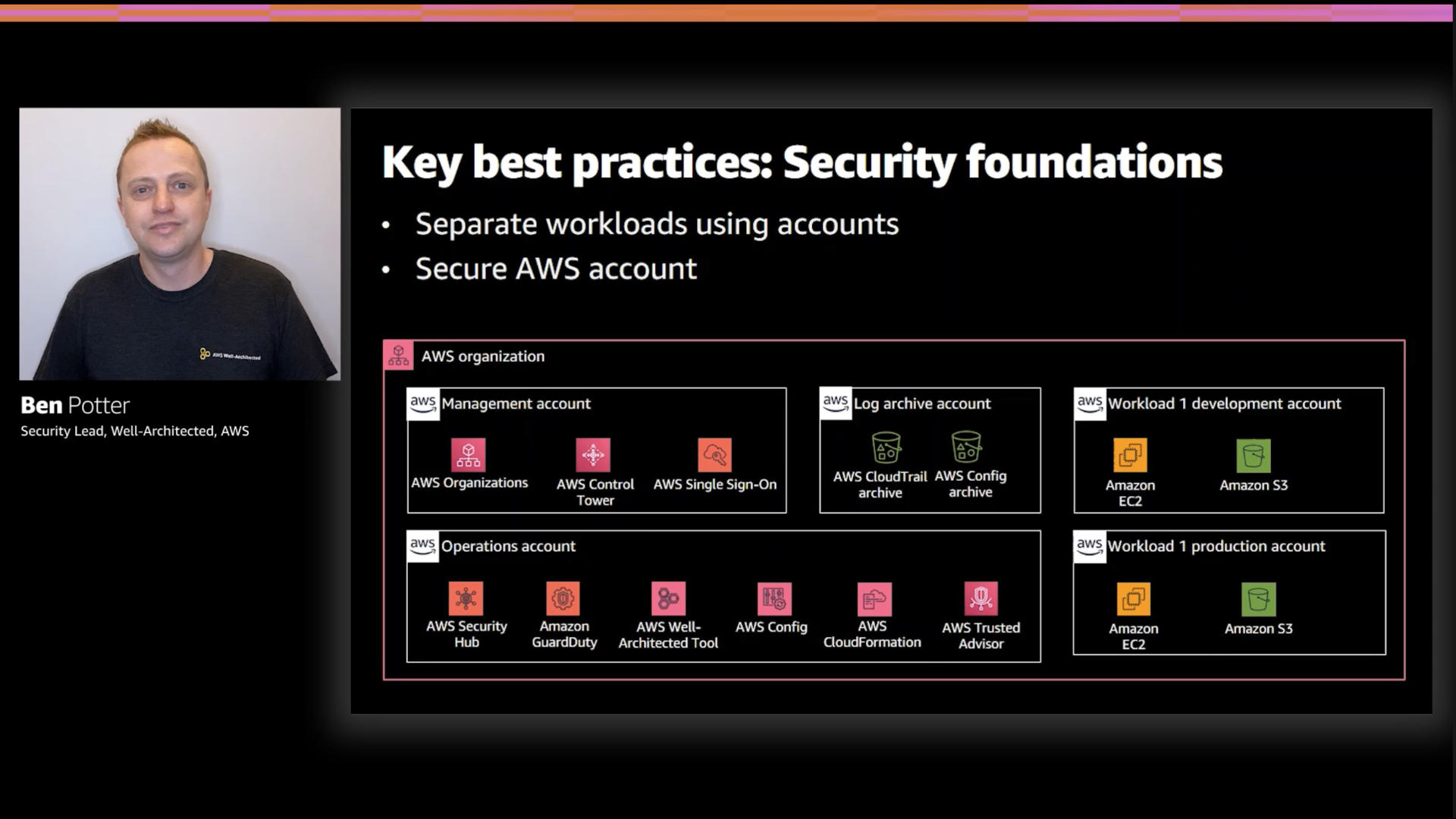
AWS Foundational Security Best Practices standard This standard helps you continuously evaluate all of your AWS accounts and workloads, and quickly identify areas of deviation from best practices. It provides ... Establishing your best practice AWS environment WebThe framework described on this page represents AWS best practices that you should use as a starting point for your AWS journey. To get started, refer to the AWS Organizations Getting Started Guide to build your own multi-account AWS environment. Alternatively, you can use AWS Control Tower to help you quickly set up a secure initial AWS environment … AWS Well-Architected - Build secure, efficient cloud applications AWS Well-Architected Partner Program members have in-depth training on the AWS Well-Architected Framework, and are empowered to implement best practices, measure workload states, and make improvements where required. Customers engaged with these partners see significant cost savings, improved application performance, and reduced security risks.
Aws best practices. Introduction - EKS Best Practices Guides - GitHub Pages Best Practices for Cluster Autoscaling: karpenter, cluster-autoscaler; Best Practices for Running Windows Containers; Best Practices for Networking; We also open sourced a Python based CLI (Command Line Interface) called hardeneks to check some of the recommendations from this guide. In the future we will be publishing best practices guidance ... ARCHIVE: Architecting for the Cloud — AWS Best Practices - Awsstatic Amazon Web Services – Architecting for the Cloud: AWS Best Practices. Page 1. Introduction. Migrating applications to AWS, even without significant changes ... Best practices for AWS accounts - AWS Account Management Best practices for managing AWS access keys Javascript is disabled or is unavailable in your browser. To use the Amazon Web Services Documentation, Javascript must be enabled. Best practices - AWS Certificate Manager WebBest practices are recommendations that can help you use AWS Certificate Manager (AWS Certificate Manager) more effectively. The following best practices are based on real-world experience from current ACM customers.
AWS CloudFormation best practices - AWS CloudFormation WebBest practices are recommendations that can help you use AWS CloudFormation more effectively and securely throughout its entire workflow. Learn how to plan and organize your stacks, create templates that describe your resources and the software applications that run on them, and manage your stacks and their resources. Security best practices for Amazon S3 WebEnable AWS Config. Several of the best practices listed in this topic suggest creating AWS Config rules. AWS Config enables you to assess, audit, and evaluate the configurations of your AWS resources. AWS Config monitors resource configurations, allowing you to evaluate the recorded configurations against the desired secure configurations. Using … Best practices for Amazon EC2 - Amazon Elastic Compute Cloud Establish credential management policies and procedures for creating, distributing, rotating, and revoking AWS access credentials. For more information, see IAM Best Practices in the IAM User Guide. Implement the least permissive rules for your security group. Learn best practices for securing your AWS account and resources Aug 22, 2022 ... Safeguard your passwords and access keys · Activate multi-factor authentication (MFA) on the AWS account root user and any users with interactive ...
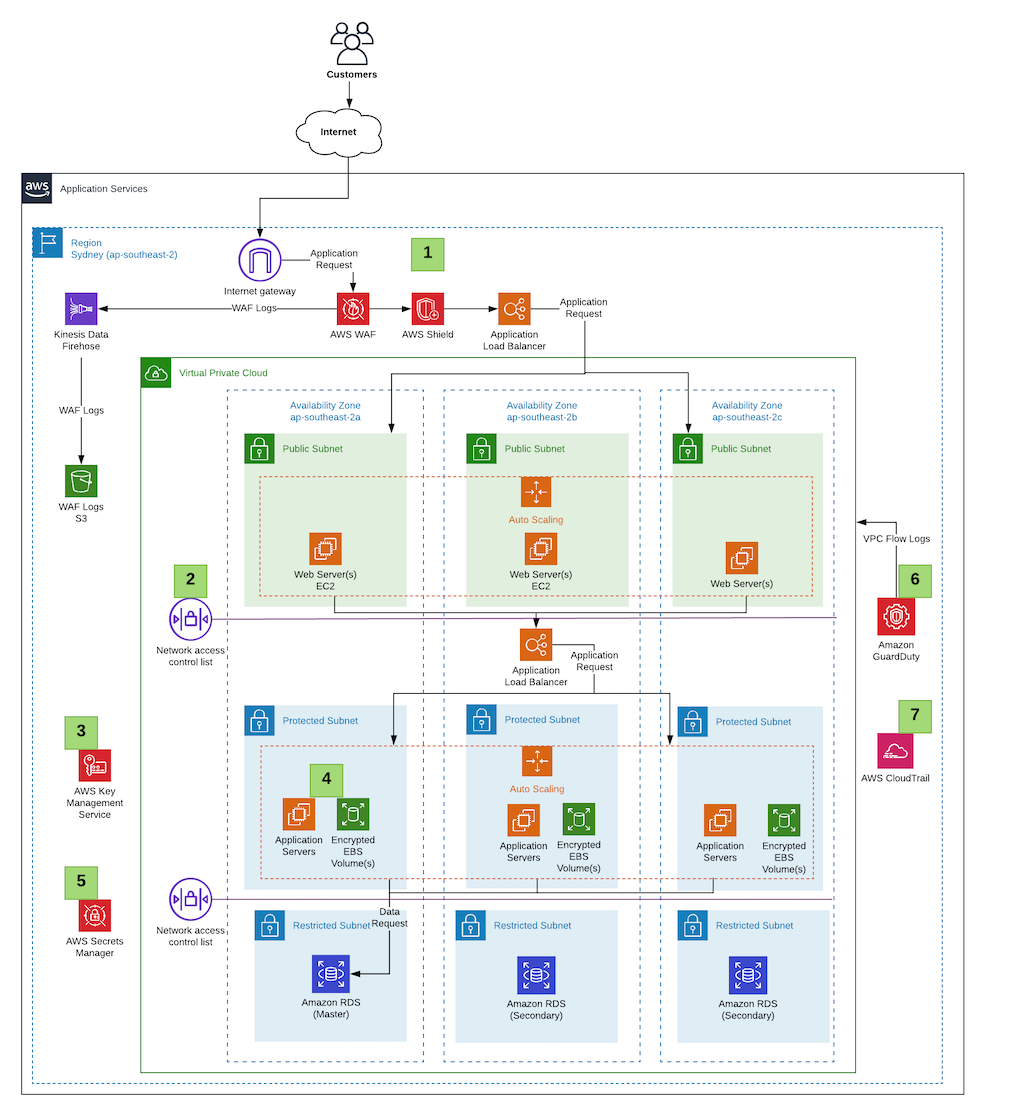
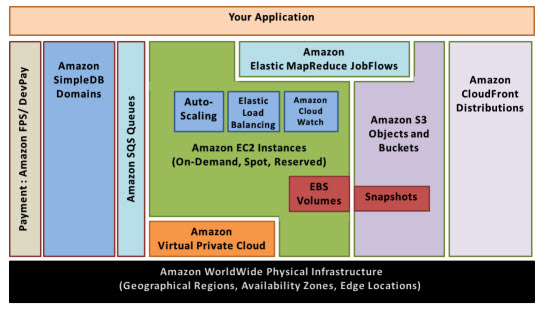
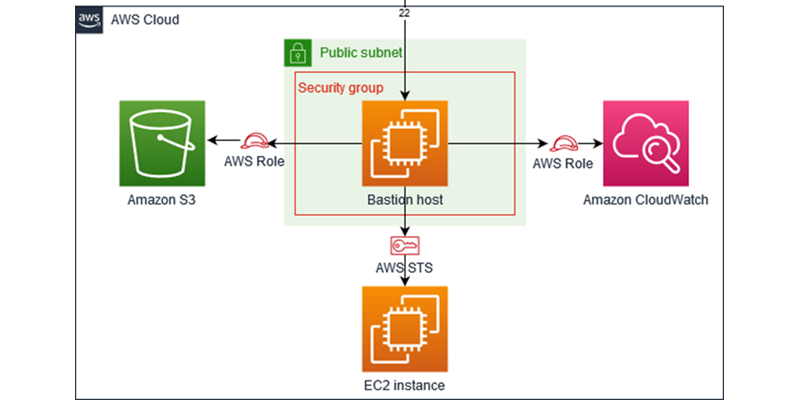
Best practices for Amazon EC2 - Amazon Elastic Compute Cloud WebBest practices for Amazon EC2. To ensure the maximum benefit from Amazon EC2, we recommend that you perform the following best practices. Security. Manage access to AWS resources and APIs using identity federation, IAM users, and IAM roles. Establish credential management policies and procedures for creating, distributing, rotating, and … AWS Security Best Practices WebAWS. See Security Best Practices in IAM for more information. Regions, Availability Zones, and Endpoints You should also be familiar with regions, Availability Zones, and endpoints, which are components of the AWS secure global infrastructure. Use AWS regions to manage network latency and regulatory compliance. When you store data in a … Establishing your best practice AWS environment - Amazon AWS Your OUs should be based on function or common set of controls rather than mirroring your company's reporting structure. AWS recommends that you start with ... AWS Best Practices: five key approaches - Cloud Academy May 27, 2015 ... 4. AWS Best Practices: use the Trusted Advisor · Service Limits Check · Security Groups – Specific Ports Unrestricted Check · IAM Use Check · MFA on ...
Security best practices for Amazon S3 Amazon S3 provides a number of security features to consider as you develop and implement your own security policies. The following best practices are general guidelines and don’t represent a complete security solution.
Best practices for working with AWS Lambda functions WebREPORT RequestId: 3604209a-e9a3-11e6-939a-754dd98c7be3 Duration: 12.34 ms Billed Duration: 100 ms Memory Size: 128 MB Max Memory Used: 18 MB. By analyzing the Max Memory Used: field, you can determine if your function needs more memory or if you over-provisioned your function's memory size.. To find the right memory configuration for your …
AWS Security Best Practices AWS Security Best Practices. PDF. Notice: This whitepaper has been archived. For the latest technical information on Security and Compliance, ...
Follow Security Best Practices as You Configure Your AWS Resources Jun 8, 2017 ... Best practices to help secure your AWS resources · Create a strong password for your AWS resources · Use a group email alias with your AWS account.
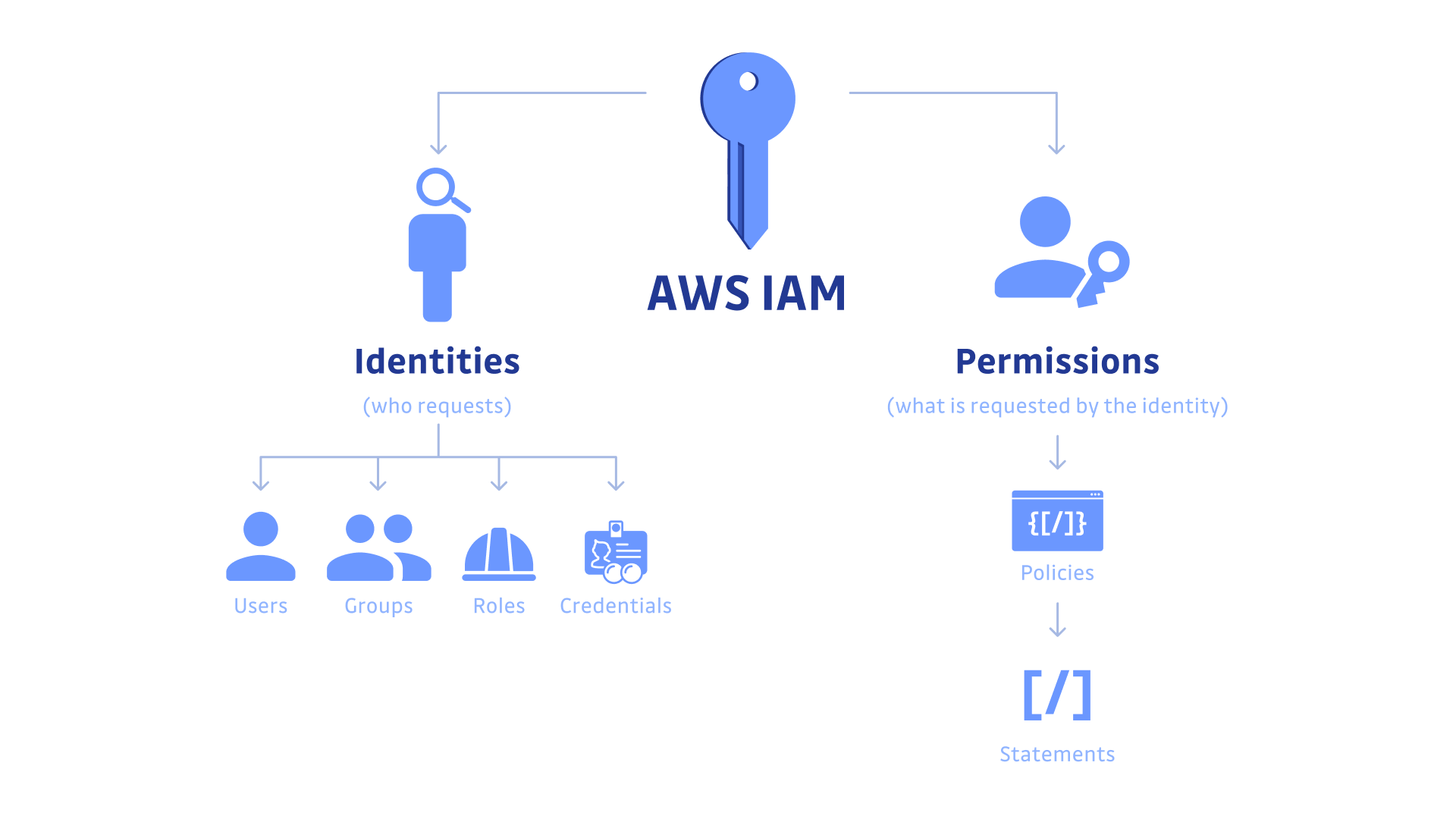
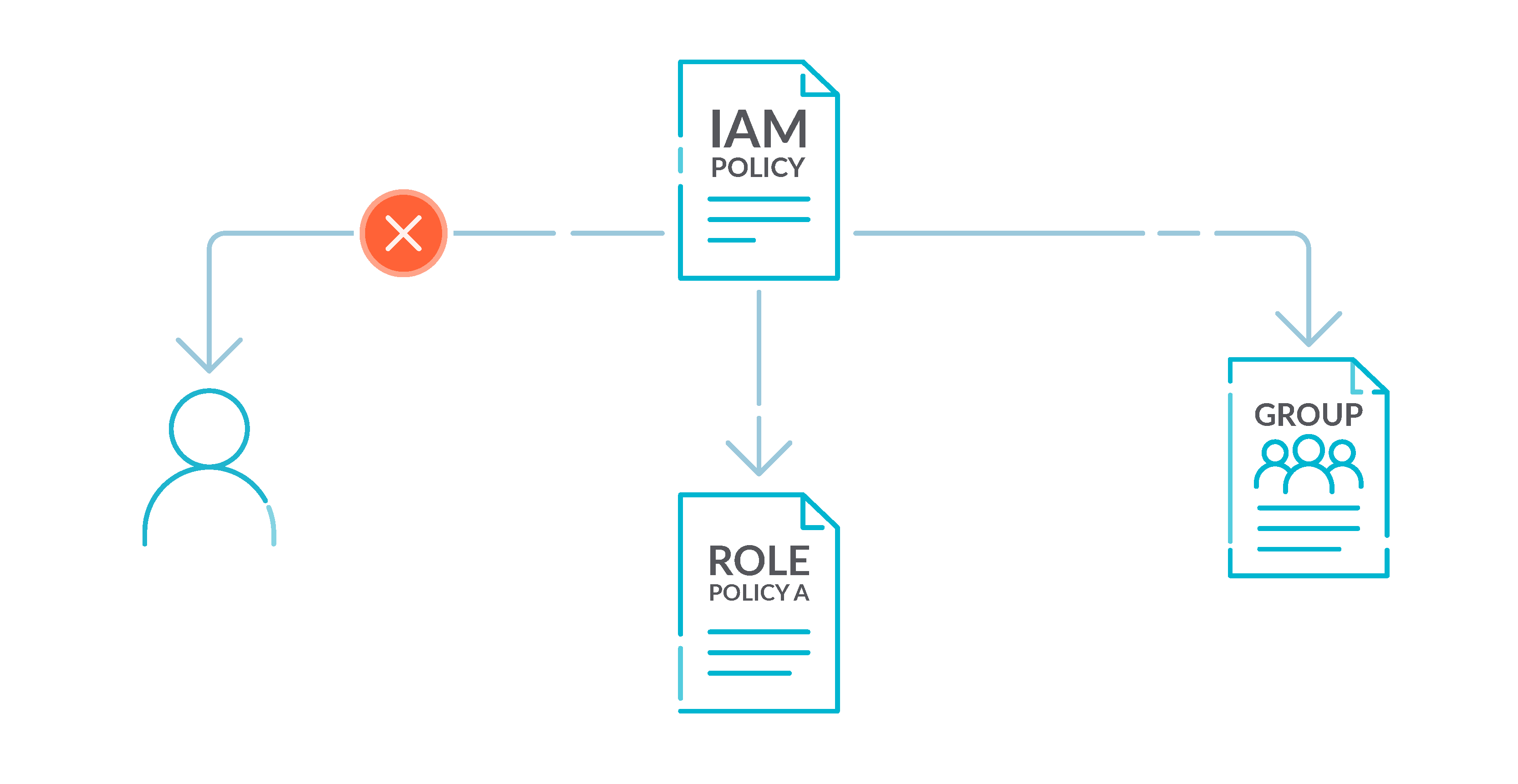
Security best practices in IAM - AWS Identity and Access … Web14/07/2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide.
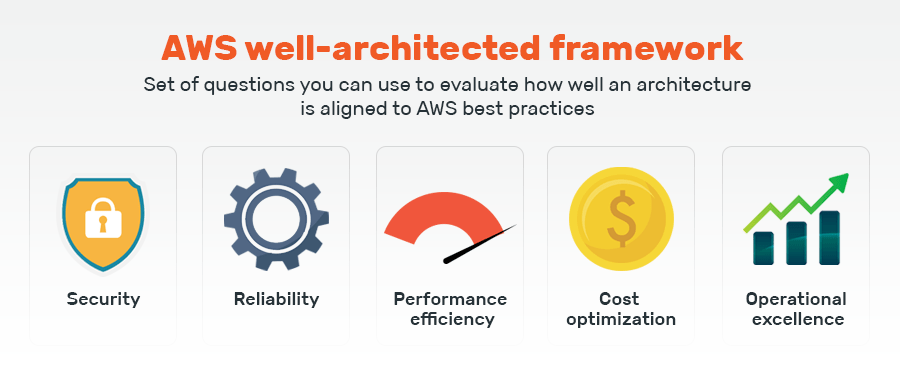
Best practice - AWS Well-Architected Framework Best practices are approaches, processes and methods that have been shown to lead to good outcomes. These are identified by looking at sets of outcomes and ...
Security best practices in IAM - AWS Identity and Access ... Jul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide.
AWS Well-Architected - Build secure, efficient cloud applications AWS Well-Architected Partner Program members have in-depth training on the AWS Well-Architected Framework, and are empowered to implement best practices, measure workload states, and make improvements where required. Customers engaged with these partners see significant cost savings, improved application performance, and reduced security risks.
Establishing your best practice AWS environment WebThe framework described on this page represents AWS best practices that you should use as a starting point for your AWS journey. To get started, refer to the AWS Organizations Getting Started Guide to build your own multi-account AWS environment. Alternatively, you can use AWS Control Tower to help you quickly set up a secure initial AWS environment …
AWS Foundational Security Best Practices standard This standard helps you continuously evaluate all of your AWS accounts and workloads, and quickly identify areas of deviation from best practices. It provides ...





























0 Response to "43 aws best practices"
Post a Comment